We’re going to be discussing database parameters that if not set correctly, it will allow hackers full access to the database.
Oracle database security quick tip.
Oracle Privilege Analysis for testing, before moving to production. #LeastPrivilege #Infosec #Oracle #Privileged

In the testing phase, we normally test functionality and break the application. There is something that’s missing. Now, most developers are not experts in how privileges work in Oracle, this is not a bad thing because privileges can be complex to implement. Because of this, applications frequently are moved into production over privileged. Addressing over privileged applications is really not all that difficult to accomplish, it just takes some time.
The basics:
- To run dbms_privilege_capture you’ll need to grant the CAPTURE_ADMIN role to the user running dbms_privilege_capture.
- dbms_privilege_capture can capture in four modes:
- G_DATABASE mode: will capture all privileges used in the database. I use this one a lot to get a broad picture of what privileges are being used in the database.
- G_ROLE mode: will capture all access to specific roles. Will capture the usage of a role.
- G_CONTEXT: will capture the privileges used when a context test is true .
- G_ROLE_AND_CONTEXT: will capture privileges used when a context test is true and a role is used.
- The create_capture procedure creates a capture policy that defines the conditions when the privilege is captured, along with giving a name for the capture.
sys.dbms_privilege_capture.create_capture(
name in varchar2,
description in varchar2,
type in varchar2,
roles in varchar2,
condition in varchar2);- The enable_capture procedure After you’ve created the capture policy, you’ll need to enable it to start the capture. For the first run, I normally create the capture policy, then enable the capture in the same PL/SQL block.
sys.dbms_privilege_capture.enable_capture(
name in varchar2,
run_name in varchar2 default null
);
- disable_capture: After you’re done capturing privileges, you’ll need to disable the capture, so you can generate the results. The only parameter is the name parameter.
sys.dbms_privilege_capture.disable_capture(
name => 'check_beckys_use_of_processor_and_cashier'
);
- generate_results: Once you’re done capturing the privileges for a run, we need to generate the results. The overhead of running privilege capture is pretty low; however, generating the results will take some CPU and may take a few seconds to finish, depending on how long the privilege capture ran.
sys.dbms_privilege_capture.generate_result(
name in varchar2
run_name in varchar2 default null
dependency in pl/sql boolean default false
);
- drop_capture: After a while, just like anything else, you’ll want to clean up old captures. To do that, you’ll need to drop them. It’s quite simple, just execute the following.
begin
sys.dbms_privilege_capture.drop_capture(name => ‘<capture name>’);
end;
/
Oracle provides the rdms_privilege_capture package and views so you can access what privileges are actually being used by an application. I use cytoscape (open source) to visualize complex role highicarcies and see just where I can prune excess roles and privileges.
Now that we got that out of the way, let’s look at the output. Because we’re using this in testing the software, the focus is on finding out where you can adjust your privileges to achieve least privilege.
SYS.DBA_UNUSED_PRIVS to view any privileges that are unused. You’ll want to put some focus here to trim out privileges that are not being used in your testing.
DBA_USED_PRIVS to view the privileges that were used during your testing. You may find that some of the roles can be broken down to fine grained roles and use role hierarchies, or go the opposite direction and consolidate roles.
DBA_USED_SYSPRIVS to find system privileges that were used during your testing.
DBA_USED_OBJPRIVS to find object privileges that were used during your testing.
DBA_USED_USERPRIVS to find user privileges that were used during your testing.
DBA_USED_PUBPRIVS to find user privileges that were used during your testing. Now, my practice has been to revoke public privileges whenever possible, grant those privileges to named roles, then grant those roles to users.
There are quite a few other views that you can look at to remove unused privileges these include: DBA_UNUSED_PRIVS, DBA_UNUSED_SYSPRIVS_PATH, DBA_UNUSED_SYSPRIVS, DBA_UNUSED_OBJPRIVS_PATH, DBA_UNUSED_OBJPRIVS, DBA_UNUSED_USERPRIVS_PATH, and DBA_UNUSED_USERPRIVS.
I’ll dig deeper into these in a later post.
Data is the king, what to expect in 2022

May 6, 2017 the Economist published an article that data is more valuable than oil. https://www.economist.com/leaders/2017/05/06/the-worlds-most-valuable-resource-is-no-longer-oil-but-data
Every year I “try” to figure out what tools I need to sharpen, what tools I need to pick up, and what tools can be put away. I’ll stay focused on database security, pick up some new tools, work on improving my writing, videos, and get consistnat with the interviews . Hey, if you can’t communicate, then you can’t help the customer.
The database is not going away anytime, so we need to get serious about protecting the crown jewels we store in our databases. With my work, I still see encryption implementations that are wrong, where data will spill out unencrypted. Y’all, you need to understand how the technology you’re working with operates and configure it securely. That said, the safest place for data seems to be in the Oracle Cloud where if you’re using autonomous databases, they will be configured securely. If you’re using Infrastructure as a Service, you’ll still need to do the secure configuration and patching.
Ransomware is here to stay. We’ve seen that the most common way to access systems is through an initial phishing attack. It’s critical that users are trained and tested on phishing attacks. I hate to say it but make the users paranoid about clicking links and opening pdf documents. Frequently if I receive a link from someone, I’ll contact them out of band to check to see if they actually sent me that link. Other times a link comes from an entity that I have some business relationship with. Here I’m careful not to click a link unless I know it’s safe. Hover you mouse of the link and see where it’s directing you to. Organizations need to get serious about their backups and testing their recovery. Oracle has a couple of products that’ll give you immutable backups and air gaped backups. I’ll be writing about them later once I’ve had a chance to test them.
I have a daily habit of figuring out what’s not working and adjusting. Seems like sometime things just slowly creep up on you and you don’t notice it. Well, I took the last two weeks off for the holidays and put my mind to what is not working, because to be honest, my focus does not seem to be as good as it’s been in the past. I’ve also noticed, that although I love working from home and enjoy the solitude, I’m craving being around people more and more. Now, working from home as cut out my commute time, saving me over three hours a day that I can use for more productive things, however; I’ve also cut way back on my travel and have not been able to spend time with friends and work associates. This isolation has impacted my ability to focus on writing and getting my thoughts down on paper. Now, every morning, I spend about thirty minutes to an hour writing. This process allows me to clear my head, get my ideas straight, and identify gaps in my knowledge. What is missing are those long conversations with people smarter than me that triggers ideas. So, in 2022, I’m going to spend a lot more time traveling to see friends. And sense I’m telecommuting, that will not be a problem. Just give me a room, fast internet, and coffee, I’ll get the work done. So, if you see me popping up in your city, don’t be surprised. That’s just me stopping my isolation.
Tech to watch in 2022:
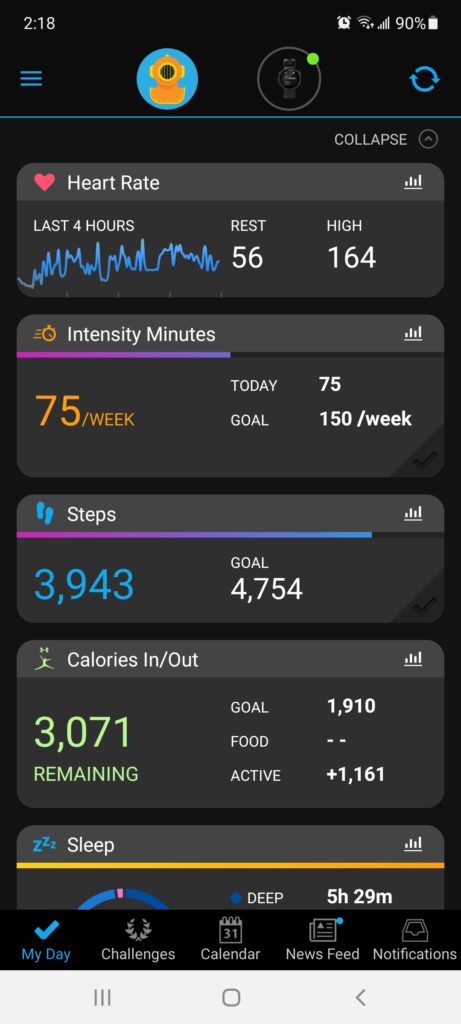
VR Fitness Apps. Face it, gym burnout is a real thing. My exercise of choice has always been to hit the weights, and every few months I get burnt out and must force myself to exercise. Always telling myself that the hormones released are not only good for my body; however, they are also good for my brain health. For the last couple months, I’ve been using www.supernatural.com, a VR aerobic workout that places you in some of the most beautiful places in the world. This makes it more fun to exercise, and considering that my work puts me at my desk for up to ten hours a day, using my brain; that exercise is important to my ability to produce, and my health. Note: my resting heart rate using just weights was always around 75bpm, after two months using supernatural, my resting heart rate averages around 61bpm and frequently drops down to 50bpm. Now, considering I’m 61 years old, and my family has a history of stokes in their 60’s (my younger brother had a stroke the week before Christmas 2021!) This is another good reason for aerobic and weight training. Now, one thing I like about supernatural is the mix up in exercises, one of the things I don’t like is not having the ability to fine tune the intensity of the workouts. When exercising, I like being at about 104%, this way I’m always pushing. But from what I’ve found, you don’t have the ability to fine tune, what you get is what you get.
Electric flying taxis. I’m not too sure about this one, but I’m seeing more startups moving into this space. The problem is the weight and capacity of the batteries. So, if we do see these start to fly in cities around the world, they’ll likely be for very short hops.
Quantum computing. I’ve always had an interest in quantum mechanics, mostly because it’s so mind bending. IBM https://www.ibm.com/quantum-computing/ now has the 127 qubit processor. We’re making some big leaps but I’m thinking, what will be the killer app. Will it be Quantum AI? That’s where my money is.
Cybersecurity, culture, travel, and keeping your IT infrastructure safe.
I get to chat with Liron Amitzi and Jim (The Why Guy) Czuprynski about what interest me the most. Keeping your IT infrastructure safe and culture.
Transparant Data Encryption and Oracle Key Vault with Peter Wahl.
I had the pleasure of chatting with Peter Wahl, Oracle Principle Product Manager for Encryption and Secrets. He gives a great talk on Transparent Data Encryption and Oracle Key Vault.
Unified Audit and Virtual Private Database
It seems not a day goes by where I’m not humbled in some way or another. Frequently this happens due to limits of my knowledge or something I’d forgotten. There is a wrinkle when you combine Unified Auditing and Virtual Private Databases (VPD).
Here’s the setup.
create or replace package HR.hr_vpd_policy as
function hr_emp_vpd_policy (p_schema varchar2,
p_table varchar2)
return varchar2;
end;
/
-- keep it real simple. just return
-- department_id = 10.
create or replace package body HR.hr_vpd_policy as
function hr_emp_vpd_policy (p_schema varchar2,
p_table varchar2)
return varchar2 is
p_ret_val varchar2(255);
begin
p_ret_val := 'department_id = 10';
return p_ret_val;
end;
end;
/
begin
sys.dbms_rls.add_policy (
object_schema => 'HR',
object_name => 'EMPLOYEES_VIEW',
policy_name => 'HR_EMP_SEL_POL',
function_schema => 'HR',
policy_function => 'hr_vpd_policy.hr_emp_vpd_policy',
statement_types => 'SELECT'
);
end;
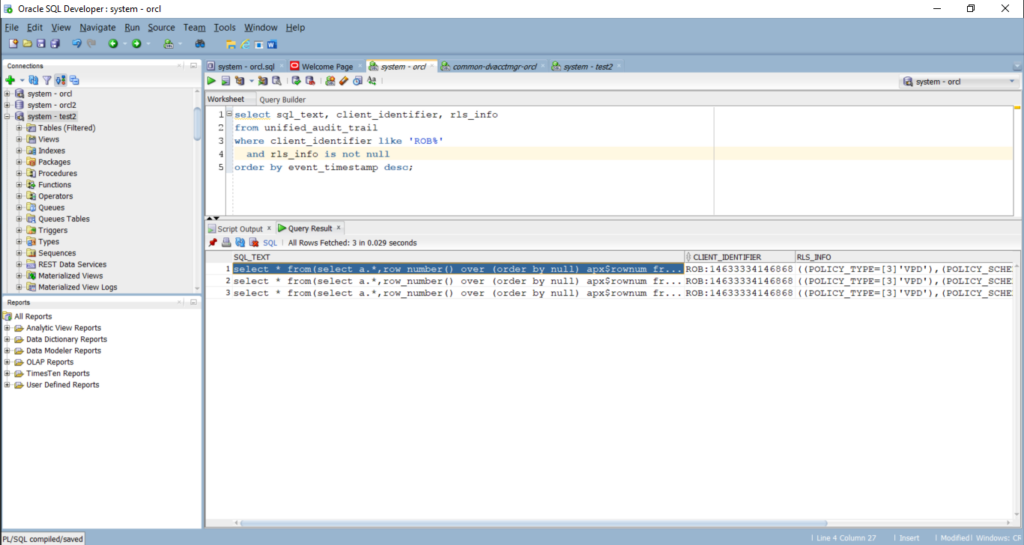
/Here’s the question. How do I know the where clause VPD placed on a sql statement? Well it’s not in the sql_text column (like I thought is was), it is in the rls_info column. Remember, VPD was called “Row Level Security.” Oracle changed it’s name sometime back, I think 10g, but don’t quote me on the version Oracle changed the name.

Do you want to know where I’ll be speaking this fall?

Where am I speaking this fall? Poland and Croatia conferences have been confirmed. Waiting for Spain, and ECOUG. Let’s get back to normal and be safe about it. Looks like I’ll be busy for the next several months. Life is good.
Warsaw Poland September 10 – 11. https://poug.org/en/
Rovinj Croatia October 12 – 16 https://2021.hroug.hr/eng
Madrid Spain November 11 https://spoug.es/spoug21/
ECOUG November 1-3 https://www.eastcoastoracle.org/
There has been some changes. #Accenture #DatabaseSecurity #InfoSec

Life is busy and good; new Some of y’all may already know, after almost thirty years of working for myself, I accepted a position with Accenture Enkitec Group as Technology Innovation Principal Director and the Global Lead for Database Security. There are a lot of reasons I accepted this position. Primarily, I’ve known the folks from Enkitec for a number of years; they have always impressed me with their knowledge, willingness to share that knowledge, and they get s&*t done. Being part of a global team that is focused to delivering the best for the customer. The opportunity to learn new things; now that’s a big plus for me.
Now, being an employee it’s really new to me, they have these things called HR, People Leads, and policies. Who knew? My People Lead was always my bathroom mirror where I would have long discussions with myself about my future and where I needed to put my focus. Now, I have someone else who I can discuss direction, where my focus should be, and also promote me within and outside of Accenture. This is great! Yea’ even I need to get pointed in the right direction every now and then.
New talks are coming up in Poland, Croatia, North Carolina, Spain, East Coast Oracle Users Group (ECOUG). I’m waiting for acceptance from Croatia, ECOUG, and need to get my abstracts in for Spain. Stay tuned for more details on what talks I have coming up.
Upcoming talks UTOUG, INSYNC, and Uzbekistan INHA University.
March and April are booking up fast. Getting real busy and loving life.
Utah Oracle Users Group (UTOUG) March 17 – 18 Keynote: “Curves ahead: Emerging technology threats.”, “Holistic Database Security in the cloud.”, and “PL/SQL Secure Coding in the cloud.”
INSYNC Tuesday March 30 and April 1 “Holistic Database Security in the Cloud.”
Uzbekistan INHA University April 6. “Staying Current in a Constantly Changing IT Environment.”
The Future of #AI with Sandesh Rao
In our series on the future of AI, here is the interview with Sandesh Rao, VP Autonomous Health and Machine Learning at Oracle
Here is the registration link in Russian and English
Here is the English language registration link.
https://docs.google.com/forms/d/e/1FAIpQLSd6Uz5KWkHnnmY0u8X-jIruX2a0bGWSM9QUrVTCvCplq29Llw/viewform
And November 2, I will be speaking at the East Coast Oracle Users Conference on Holistic Database Security. Bellow is the registration link.
